A friend last week seriously compared the Corona vaccine research with the need to use their cloud-based solution (Source). But is “The Cloud” a panacea? And what does that question have in common with consulting? Or with outsourcing? COTS or tailormade, DIY or expert job? Consulting, outsourcing or cloud?

The Consulting Rule
My mantra for many years has been that consulting is a short-term (high paid) business. Either you have a short-term, a peak demand in a certain know-how, then you hire a consultant. Else, you better have or develop your own expertise. To which a consultant may contribute. Most (not all) consultants being in a company for more than a year without helping the company to develop the necessary know-how are leeche(r)s.
Outsourcing
 For outsourcing, it is very similar. If you have little need for a certain specialization, you outsource to experts and consultants. That can be i.e. tax management in small companies, HR, IT, etc. In this case, it is less about consulting, but about consolidation.
For outsourcing, it is very similar. If you have little need for a certain specialization, you outsource to experts and consultants. That can be i.e. tax management in small companies, HR, IT, etc. In this case, it is less about consulting, but about consolidation.
One common example would be the ground handling at your base (should be in-house) or at an outstation (outsourced). Though even at your base, if uncommon in your geo, you might outsource i.e. deicing to the airport, not serving just you, but all airlines operating at that airport using a central deicing pad.
Anything vital to your business, you better have the expertise in-house.
Cloud Computing
 Cloud computing is another area of (IT) outsourcing. It follows the same rules. So if you are a very small airline, you will likely take Commercial of the Shelf (COTS) IT-solutions. You use some passenger service solution (PSS), an OPS system, the airports’ check-in management system, etc.
Cloud computing is another area of (IT) outsourcing. It follows the same rules. So if you are a very small airline, you will likely take Commercial of the Shelf (COTS) IT-solutions. You use some passenger service solution (PSS), an OPS system, the airports’ check-in management system, etc.
But this comes with a benefit and a burden. The benefit being “commonality”, you can likely find experts that learned those tools in their previous company. You don’t need to bother about installation, server-management, etc., you entrust this to the partner. But that can also backfire, if that partner does not have sufficient infrastructure. Most major airline-wide groundings in the past years were not weather, but IT based. A single “outsourced” system not functioning as it should, such taking down the airline’s IT.
Further, you entrust your vital data to “someone else”. And I have seen that against all agreements, how that data was and is being used to do “own analysis”. You give someone else insight in mission critical information. Yes, if you are small, this might be your only choice. If you’re big, why would you do that?
Information Silos
 The main reason, I see consulting, outsourcing and cloud computing critical is the development of information silos. Not you own the important information, but “someone else”, someone outside your company. It can be a consultant, it can be a service company or an IT-system.
The main reason, I see consulting, outsourcing and cloud computing critical is the development of information silos. Not you own the important information, but “someone else”, someone outside your company. It can be a consultant, it can be a service company or an IT-system.
The second reason is that this information in all my experience is not seamless available to others, be it your own people or other IT-systems used. Especially on IT-systems, even the large players in all my experienced failed on system-independent interfaces to all data. In case of problems, most systems do not allow you an export of the raw data for your own use, much less an interactive data exchange with custom software of your own.
Researching for KOLIBRI.aero about IT infrastructure for an airline, I did not find any given integrated combination of PSS, ops system, CRM, accounting with a common, instant BI (business intelligence) analysis. Speaking to several airlines, their IT managers expressed their own frustration on that situation. Airlines having developed their own solutions, investing big secondary money into interfacing their different added “licensed systems”.
The Cloud Computing Cage Model
 My first experience with cloud computing was Sabre, Amadeus, but SAP was my personal experience with the SAAS model and it’s most negative repercussion. Good for the software provider, bad for the user. You bind yourself to the ecosphere of the software provider. For good or for bad. To change later is being made so difficult and expensive, it’s virtually impossible. Where the data might still be available, the computing “rules” are mostly not, you have to reengineer from scratch – there is a big consulting industry out there, specializing on such jobs, usually not talking about thousands in cost but millions.
My first experience with cloud computing was Sabre, Amadeus, but SAP was my personal experience with the SAAS model and it’s most negative repercussion. Good for the software provider, bad for the user. You bind yourself to the ecosphere of the software provider. For good or for bad. To change later is being made so difficult and expensive, it’s virtually impossible. Where the data might still be available, the computing “rules” are mostly not, you have to reengineer from scratch – there is a big consulting industry out there, specializing on such jobs, usually not talking about thousands in cost but millions.
This ain’t a marriage, it’s an “adhesion contract”. Be very aware who you bind yourself to.
One Size Fits All – Does It?
With a hat size of 63 cm, I can tell you that one size does not fit all. A simple truth. If you buy COTS (commercial-off-the-shelf), you get something developed for others. It might do the job, but it’s like Micro$oft Office, a panacea. Remember how long it took until they supported PDF export? Bill Gates took the bet on “America Online” and “Microsoft Network”, rejected the Internet until it was almost too late – they’ve spend a fortune to catch up. And many users could live with Wordpad, never use the abilities of Word. Or use other text editors, Google Docs, Libre Office, … Just an example.
COTS? Or Tailor Made?
Do you need a COTS suit? Or a tailored one? Can you afford the tailored one? Or will COTS be more reasonable?
Can you afford to try yourself or do you need an expert? Temporarily or strategically long-term? There is no black or white.
The choice is yours.
Food for Thought
Comments welcome!



 Recent Airline IT Failures
Recent Airline IT Failures Another development is the “voice assistants” at home. To give the example of Alexa. As you know, my beloved daughter is called Alexsandra, so if I would use such device it would listen in, as soon as someone addresses her. Also the Echo Dot alternatives of “Amazon”, “Echo” and “Computer” are not much safer. And meanwhile, press reported how extensive Google, Amazon and others use “their” devices not to just provide a service, but filing your commands and conversations for analysis. An intrusion to my privacy causing me to caution and not buying into them.
Another development is the “voice assistants” at home. To give the example of Alexa. As you know, my beloved daughter is called Alexsandra, so if I would use such device it would listen in, as soon as someone addresses her. Also the Echo Dot alternatives of “Amazon”, “Echo” and “Computer” are not much safer. And meanwhile, press reported how extensive Google, Amazon and others use “their” devices not to just provide a service, but filing your commands and conversations for analysis. An intrusion to my privacy causing me to caution and not buying into them.
 Meanwhile and especially with the current president who seems to lack the moral values required for someone elected into such power, the “United States” in my opinion turn from friend to foe for Europe. Or at least someone who doesn’t care about our (common) well-being. Doing the wrong things for the wrong reason. Get me right. As everywhere there are good and bad people. Listen to
Meanwhile and especially with the current president who seems to lack the moral values required for someone elected into such power, the “United States” in my opinion turn from friend to foe for Europe. Or at least someone who doesn’t care about our (common) well-being. Doing the wrong things for the wrong reason. Get me right. As everywhere there are good and bad people. Listen to  Commercially, I believe it a step back to use SaaS, which is another word for “cloud computing”. If you use SaaS, better be prepared and test what happens if the “outsider” provides corrupted data, what happens in case of a link failure – and recovery. Using different computer systems, often lousy connected increases the dependency on “others”. I can’t tell you, how often I was fighting with SaaS-companies to get access to my own data. Or how they imply that “their” data is always superior to anyone else. A-CDM anyone? CRM tools anyone? I am sure you can sing that tune along…
Commercially, I believe it a step back to use SaaS, which is another word for “cloud computing”. If you use SaaS, better be prepared and test what happens if the “outsider” provides corrupted data, what happens in case of a link failure – and recovery. Using different computer systems, often lousy connected increases the dependency on “others”. I can’t tell you, how often I was fighting with SaaS-companies to get access to my own data. Or how they imply that “their” data is always superior to anyone else. A-CDM anyone? CRM tools anyone? I am sure you can sing that tune along…![“Our Heads Are Round so our Thoughts Can Change Direction” [Francis Picabia]](https://foodforthought.barthel.eu/wp-content/uploads/2021/10/Picabia-Francis-Round-Heads.jpg)
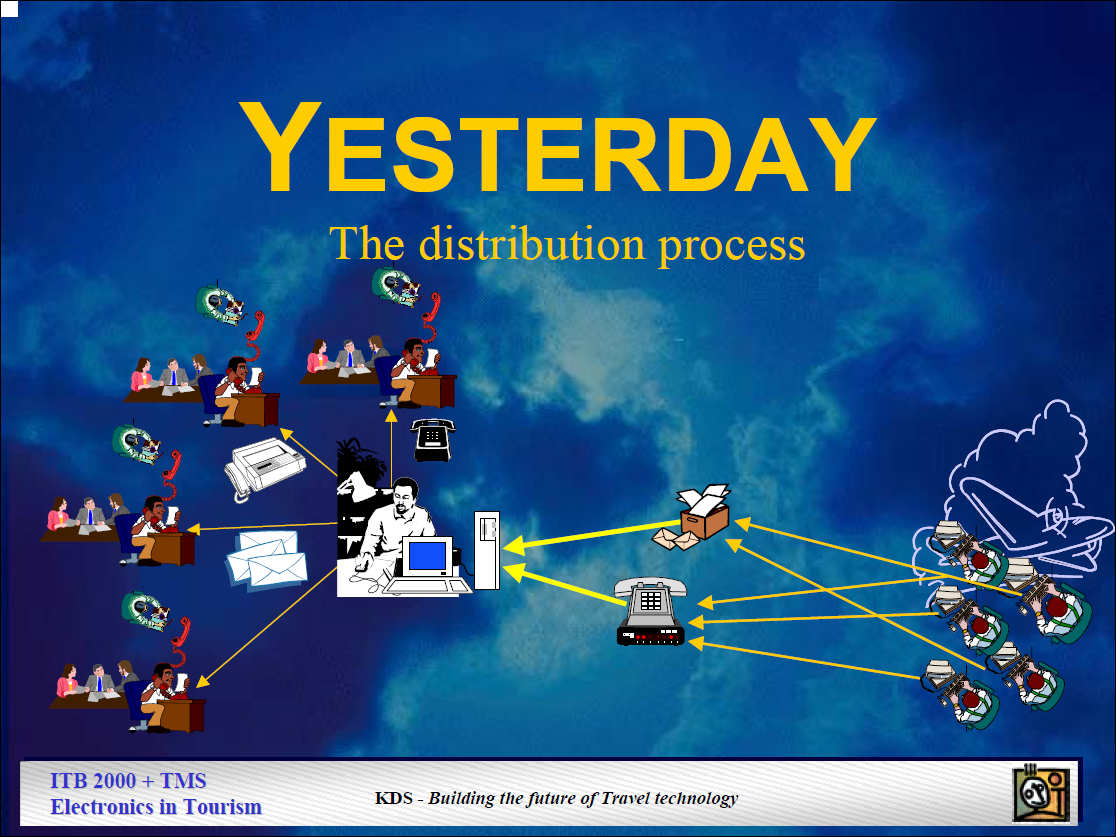 Back in 2000, in my
Back in 2000, in my 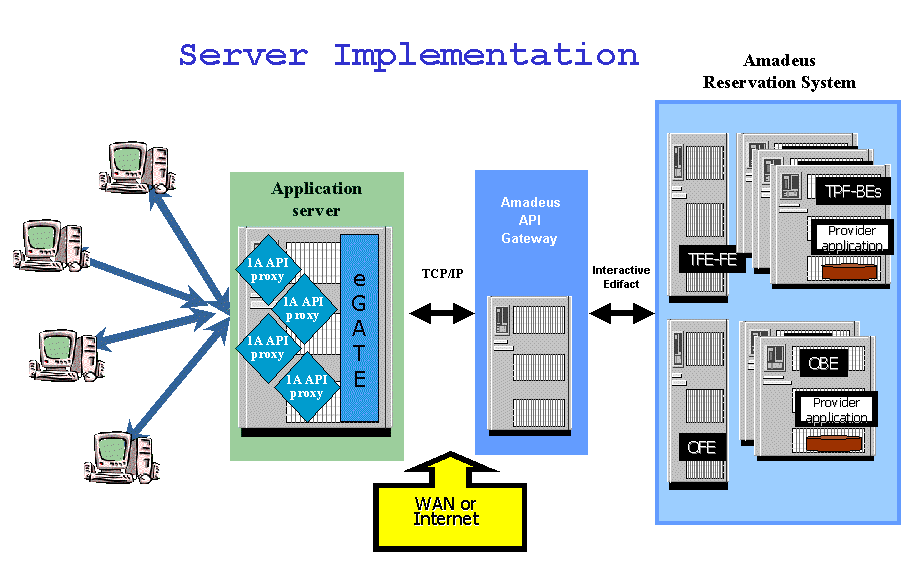

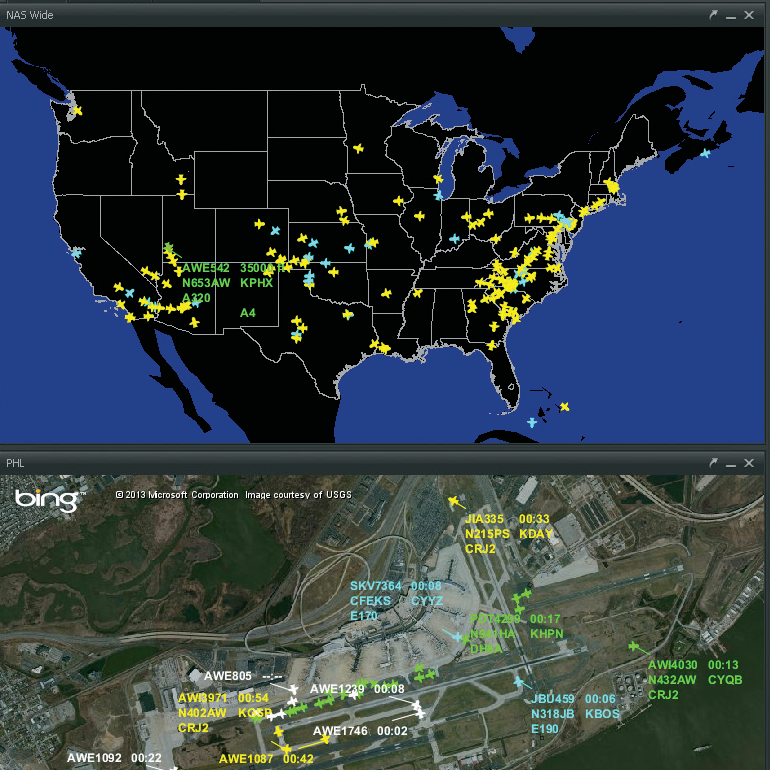 Having been pacemakers in e-Commerce, aviation today is light years behind other industries. U.S. tools showing aircraft in-flight on maps like Harris Corp. (Exelis)
Having been pacemakers in e-Commerce, aviation today is light years behind other industries. U.S. tools showing aircraft in-flight on maps like Harris Corp. (Exelis)  The last weeks the messages on LinkedIn, hyping the “Internet of Things” (
The last weeks the messages on LinkedIn, hyping the “Internet of Things” (







 To make this very clear… This is not against U.S. or Russia or Germany, we have enough problems everywhere. It is a case to point the mirror to the U.S. and Russia.
To make this very clear… This is not against U.S. or Russia or Germany, we have enough problems everywhere. It is a case to point the mirror to the U.S. and Russia.


 Lately I had quite some discussions about IT security. Is it the right thing to cut yourself off the hostile Internet? Corporate data security, data integrity?
Lately I had quite some discussions about IT security. Is it the right thing to cut yourself off the hostile Internet? Corporate data security, data integrity? In 2004, I heard a presentation that questioned the normal user to be simply ignorant to viruses, trojan horses and the most basic other means of Internet security. To date, I get hoaxes forwarded with the best of intentions. What’s a hoax? A fake threat warning. The “best” one saying “There is a virus – to delete it do this and this” and if you do this, your Windows-PC is no longer operating.
In 2004, I heard a presentation that questioned the normal user to be simply ignorant to viruses, trojan horses and the most basic other means of Internet security. To date, I get hoaxes forwarded with the best of intentions. What’s a hoax? A fake threat warning. The “best” one saying “There is a virus – to delete it do this and this” and if you do this, your Windows-PC is no longer operating.
 I was asked to address this in the blog as well. Since 2001 I use a digital e-Mail-signature provided in a cost-free web-of-trust organized by
I was asked to address this in the blog as well. Since 2001 I use a digital e-Mail-signature provided in a cost-free web-of-trust organized by  A new project in Germany is DE-Mail, said to enable “secure communication” with administration, implying “security” that simply is not there. First of all, the servers are to be maintained by German Telekom T-Systems. Second the encryption is not controlled by the user, but this is just a “secure e-Mail-address”.
A new project in Germany is DE-Mail, said to enable “secure communication” with administration, implying “security” that simply is not there. First of all, the servers are to be maintained by German Telekom T-Systems. Second the encryption is not controlled by the user, but this is just a “secure e-Mail-address”. As Blogs are a part of “social networking” and as I follow several blogs like the German
As Blogs are a part of “social networking” and as I follow several blogs like the German